Custom Security Attributes in Azure Entra ID
Navigating Azure Entra ID: Your Gateway to Seamless User Authentication with Custom Security Attributes
Custom security attributes in Entra ID make it easier to enforce detailed access control and customize user experiences directly within your identity management setup. They let you manage security and personalization efficiently by tagging users with specific attributes, ensuring your system stays adaptable and secure as your needs change.
Granular Access Control: Custom security attributes let you define and enforce precise access rules, making it easy to tailor permissions based on specific user attributes, like department or project involvement.
Simplified Management: They centralize identity-related data within Entra ID, reducing the complexity of handling external data sources and streamlining identity management processes.
Personalized User Experience: Applications can dynamically adjust features or content based on these attributes, providing users with relevant and customized interactions.
For problem statement and the overall solution:
Type of Attributes in Azure AD
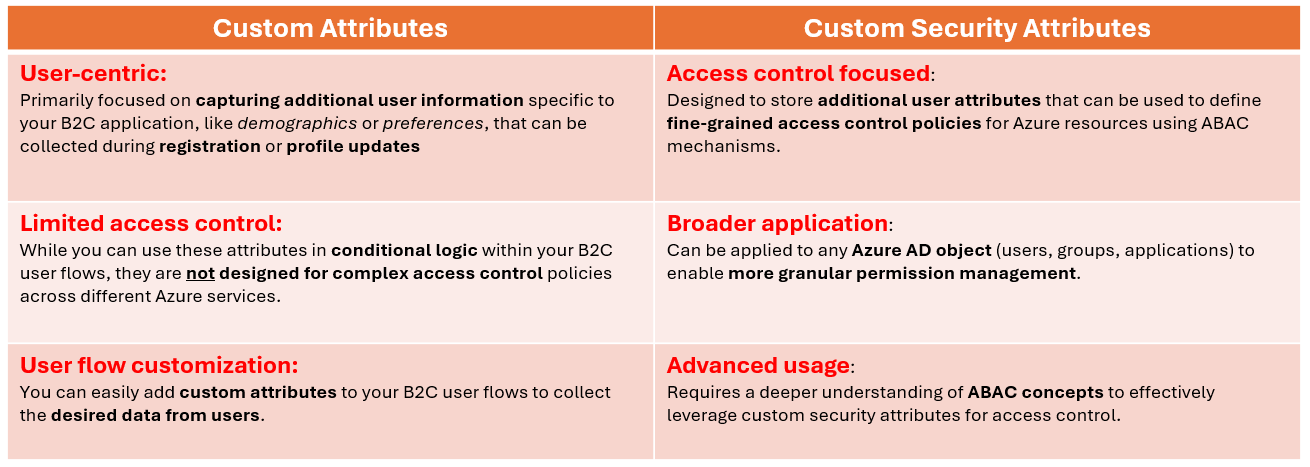
Basic Attributesrefer to the standard user profile fields provided by default (like name, email)Custom Attributesare additional data fields you can define to store specific information not covered by the basic setCustom Security Attributesare a broader category within Azure AD that allows storing business-specific key-value pairs for more granular access control, going beyond just user profiles in B2C
While both "custom attributes" in Azure AD B2C and "custom security attributes" allow for storing additional user information, the key difference is that custom attributes in B2C are primarily used to collect user data during sign-up and profile editing within the B2C tenant, while custom security attributes are designed for broader access control and granular permission management across Azure resources using attribute-based access control (ABAC) within the wider Azure AD environment.
Retrieve User Attributes from Azure AD
Prerequisites:
Azure AD Environment: An existing Azure Active Directory (Azure AD) tenant with administrative access.
Application Registration: An application is already registered in Azure AD. This application needs the necessary permissions to access user attributes via the Microsoft Graph API.
External User Invited: An external user has been invited to the Azure AD tenant. This user has accepted the invitation, granting the necessary permissions.
Adding Custom Security Attributes
Azure AD Access: The administrator logs into the Azure portal using an account with sufficient privileges (Global Administrator, at minimum).
Navigate to Custom Security Attributes: The administrator navigates to
Azure Active Directory->Custom security attributes.Create New Attribute Set: A new attribute set is created (e.g.,
teamlocation). The attribute set name and a description are provided. The type is chosen as "String," and the minimum number of attributes is set.Define New Attribute: Within the
teamlocationattribute set, a new attribute is defined. The attribute name is provided (e.g.,teamlocationasset), description, type is selected asstring, and the option to allow multiple values is selected asNo. One or more predefined values might be added (optional).Save Attribute Set: The changes to the attribute set are saved.
Assigning Custom Attributes to Users
Access Users: In the Azure portal, the administrator navigates to
Azure Active Directory->Users.Select User: The external user (Adrien, in this case) is selected.
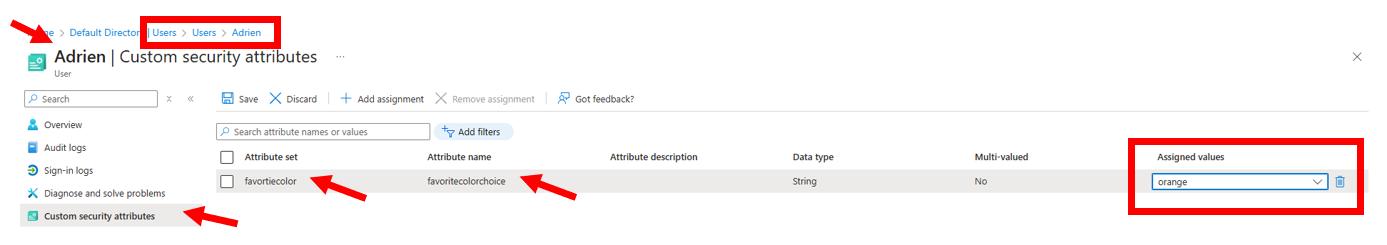
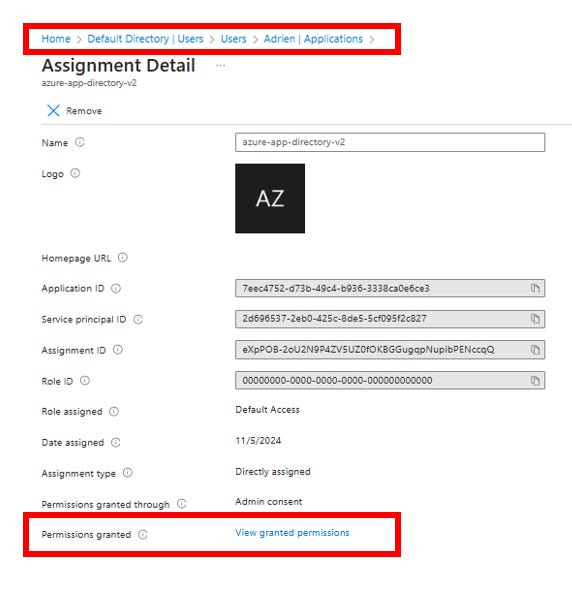
Navigate to Custom Security Attributes: In the user's properties, the administrator finds the "Custom security attributes" section.
Assign Attributes: The administrator assigns the previously created
teamlocationassetattribute to the user. A specific value from the predefined values (e.g., "Offshore") can be assigned here.
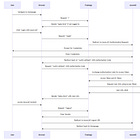
Application Code Modifications
Access Microsoft Graph API: The application's backend code uses the Microsoft Graph API to retrieve user information, including custom security attributes. It likely uses an access token obtained through Azure AD authentication.
Retrieve Custom Attributes: The code specifically requests the
teamlocationassetattribute. The API call is made within atry-exceptblock for error handling. Note that the specific Graph API endpoint and query parameters will depend on the application's requirements.Display Information: The application's frontend code retrieves the user information (including the custom attribute from the backend) and displays it in the user interface. The lines of code shown in the video's final section illustrate how to retrieve and display this data within the application.
Update the App: After the changes to the code are made, the code must be updated and redeployed. In this case, the user deploys the code to Google Cloud Run.
Verification
After the redeployment, the application successfully displays the custom security attribute ("Offshore") for the user, confirming the integration.
This detailed explanation covers the technical processes involved in using custom security attributes in an application integrated with Azure AD. The specific code snippets and API calls will vary based on the technology stack being used.
Key points to highlight
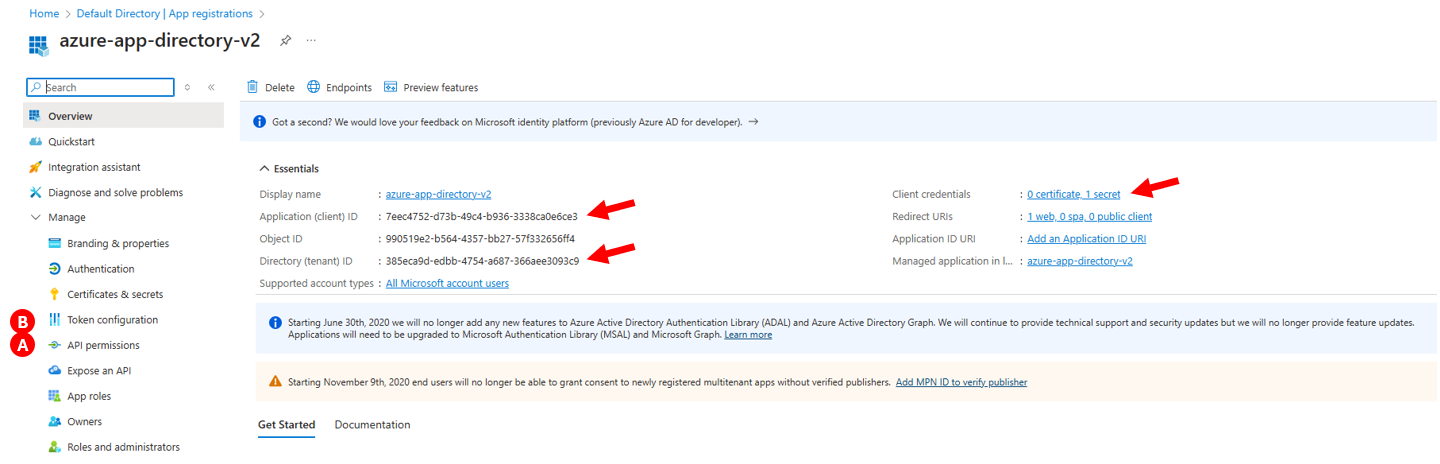
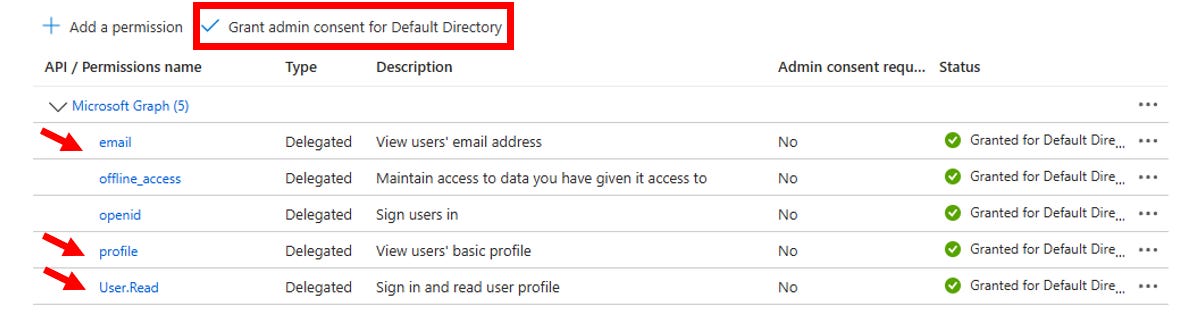
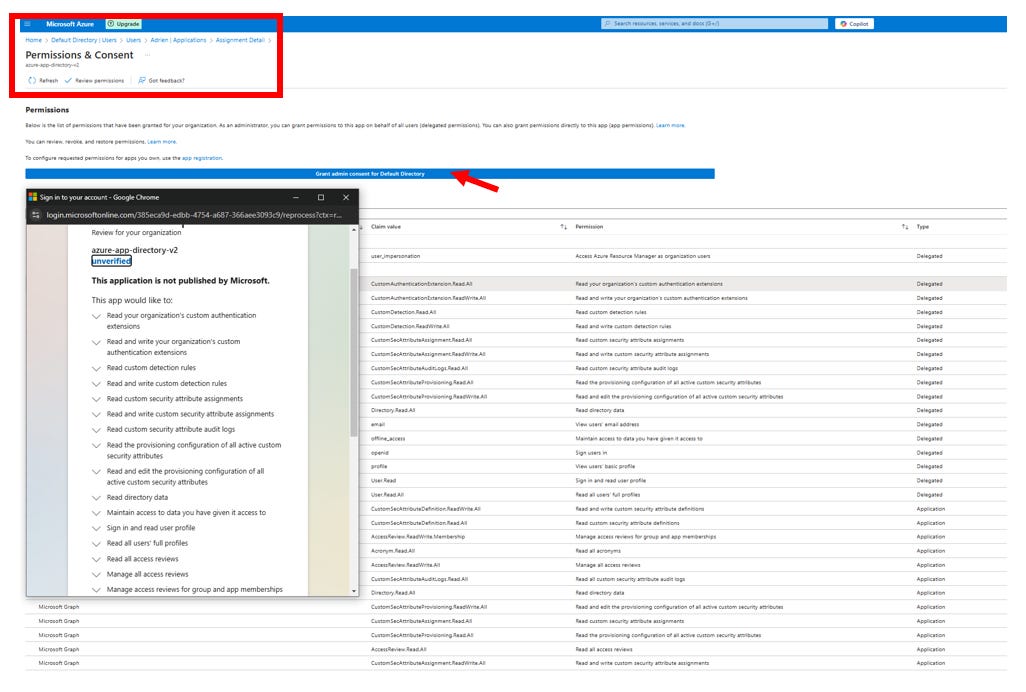
Go to API permissions (A) and ensure you have the correct permissions to read user profile information. Typically, you would need permissions like:
User.Read / User.Read.All/Directory.ReadWrite.All / CustomSecAttributeAssignment.Read.All / CustomSecAttributeAssignment.ReadWrite.All / CustomSecAttributeDefinition.Read.All / openid / profileClick Add a permission > Microsoft Graph > Delegated permissions (or
Make sure to Grant admin consent for the permissions if needed.
Configure the advanced / custom attributes
Add Custom Security Attributes:
Go to Security > Custom security attributes.
Create a new attribute set and define your custom attributes (e.g.,
favoritecolor,country,language,position, etc.)
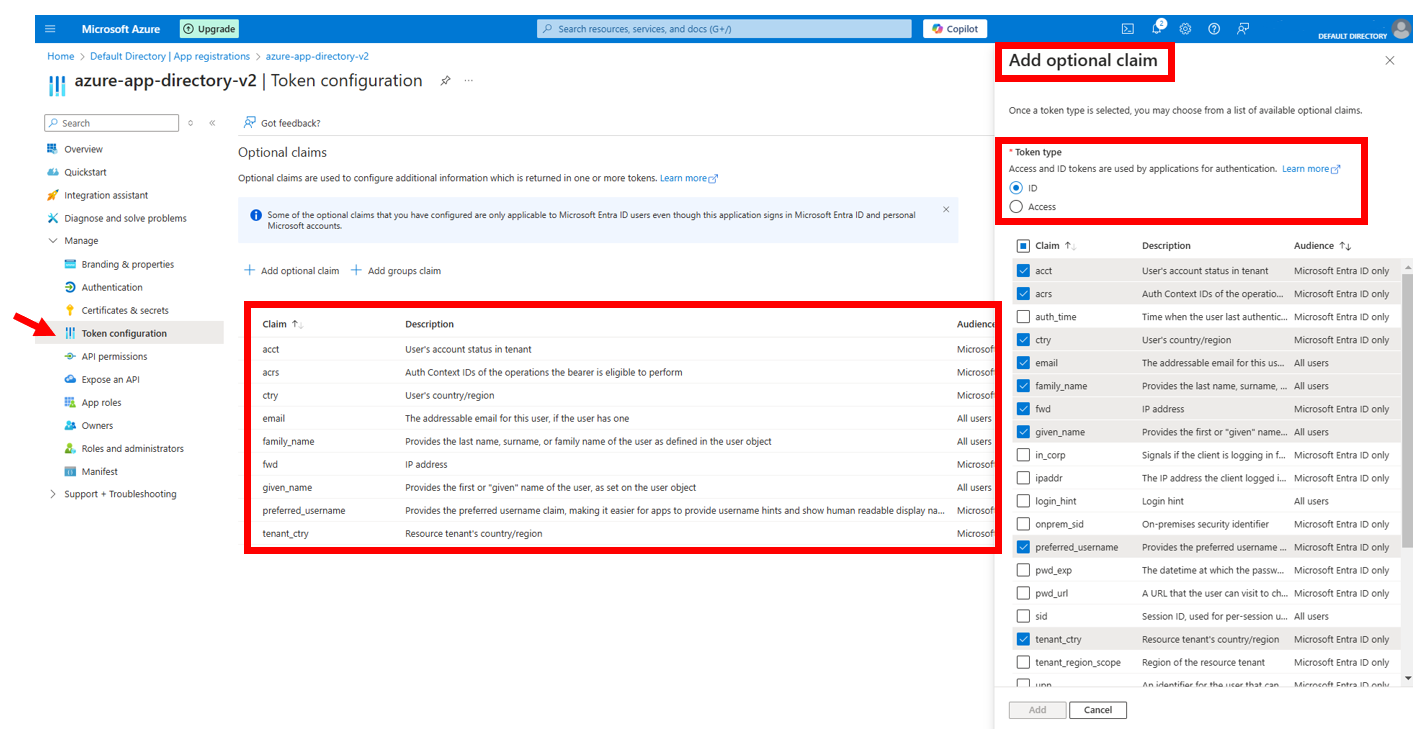
Add Custom Claims to the Token
Go to App registrations > Select your app > Token configuration.
Click + Add optional claim:
Choose the token type: ID.
Select claims like
email,preferred_username,given_name,family_name,country,locale, etc., based on the attributes you need.
Click Add to save the changes.
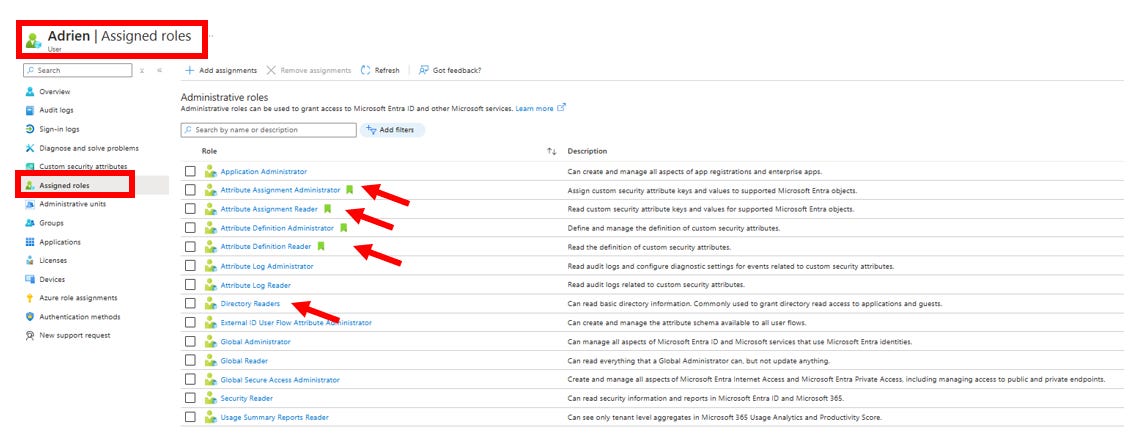
Grant the right accesses to your user
Consent the permissions
Custom security attributes in Entra ID provide a flexible way to store and manage additional data related to user identities. These attributes are particularly useful for scenarios requiring granular control over access permissions or personalized configurations based on specific attributes beyond the default user profile properties.
Tailored Access Control: Custom security attributes allow administrators to create precise access control policies. For example, you could assign attributes related to a user’s role, department, or geographical location and enforce policies that align with your organization’s security and compliance requirements.
Enhanced Personalization: Organizations can leverage custom attributes to provide personalized experiences. Applications can read these attributes and dynamically adjust content, features, or permissions based on the user’s assigned characteristics.
Simplified Identity Management: Instead of relying on external data sources or complex identity mapping, organizations can maintain all necessary identity-related attributes within Entra ID. This consolidation improves efficiency and reduces the risk of synchronization issues.
Bibliography
👉 Understanding Custom Security
👉 Managing Custom Attributes for Azure AD B2C Users
👉 What are custom security attributes in Microsoft Entra ID?